The eSIM ecosystem encompasses many actors and requires more flexibility than the SIM ecosystem, especially as risk exposure will increase with the number of connected objects that can be added through the eSIM.
The Embedded SIM (eSIM[1]) is a programmable SIM which can be remotely provisioned and integrated in any type of mobile devices whether for the consumer market (connected watches, smartphones, etc.) or the M2M market (connected meters, connected cars, etc.).
However, this evolution modifies the relationships between actors which are essential for risk and trust management in the SIM context. Typically the operator has direct contractual relationships with the SIM manufacturer which allows it to validate the SIM cards and assess its risk exposure. In the eSIM context, the loss of this direct relationship and changes in the ecosystem require new mechanisms among stakeholders – eSIM manufacturers, chipsets manufacturers, terminals manufacturers and operators – in order to maintain the security objectives.
This article shows how to meet these objectives by coupling the existing methods (i.e. certification schemes) with setting-up an organization involving stakeholders as co-actors and co-responsible for the global security. This organizational set-up, built around a new role called “Security Panel”, aims to create a security knowledge-base on the eSIM security level and a framework for authorized actors to share information related to security exposure and risk evaluation.
Associated to the certification of different technical parts of the eSIM ecosystem, risk management and decision-making processes by each stakeholder, this organization makes it possible to achieve a level of trust with the eSIM equivalent to the one with the classical SIM card.
How is the ecosystem evolving in the context of the eSIM?
The SIM is a standalone component which is independent from any device; it is marketed by the operator with all the data specific to a mobile network subscription (IMSI, network credentials and parameters, service applications, etc.) contained inside. It is the end-user that associates the SIM to the device by inserting the SIM into a device.
The eSIM is a SIM card which is remotely programmable. Hence, in most cases, it will be integrated into the device as a discrete component or in the future directly implemented into the chipset of the device. Consequently, an equipment can be marketed with an eSIM without any preinstalled connection to a mobile network. Indeed, once the device is purchased, what is called an “operator profile” can be installed and activated remotely by the end user or by a device fleet manager. The profile is the whole set of data linked to a subscription as mentioned above.
During the lifetime of the device, different profiles (for example each relevant to a different operator) can be installed and activated into the eSIM. The profiles are installed through Subscription Manager servers called “SM-DP[2]” or “SM-DP+”. These servers install the profiles via a Wi-Fi connection or via a mobile connection using a profile already available in the eSIM.
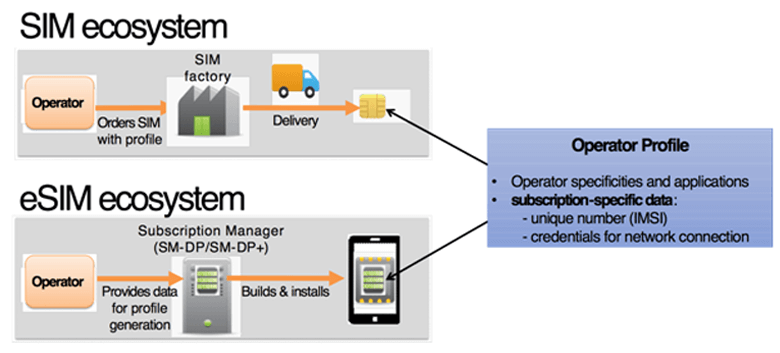
Figure 1: SIM, eSIM and operator profile provisioning
In the SIM context, the operator purchases the SIM cards and manages security aspects through validation tests and through the bilateral contract between the operator and the SIM manufacturer.
For comparison, in most cases, the eSIM is chosen by the device maker to be integrated into the device without any involvement of the operator. Therefore, generally the operator has no more the possibility to validate an eSIM type before installing its profiles, which changes the trust model in comparison with the SIM case.
Yet, because an operator profile in the eSIM enables the network access, the operator still assumes the risks relevant to the network access. The threats (e.g. profile cloning, denial of service on the network access or theft of customer data) may entail great impacts on operator reputation and revenues. In addition, considering the eSIM is built in most of the cases within the device, a security issue on the eSIM may affect the whole device, resulting in potential additional cost.
With eSIM deployment, all stakeholders – including the operators, the service providers (e.g. bank, transport), eSIM/chipset and device manufacturers – have to find a way to protect and manage the security of their assets.
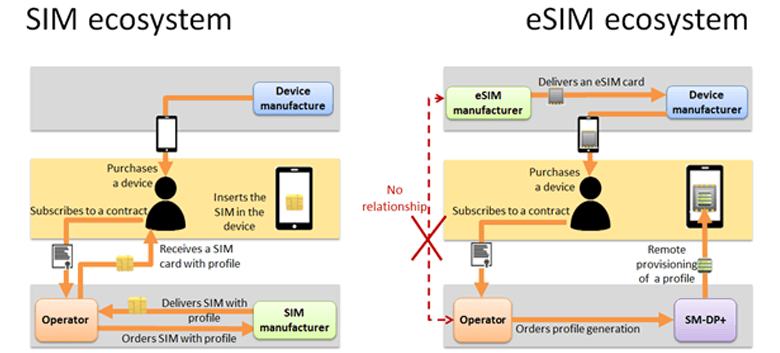
Figure 2: Responsibility shift in the eSIM ecosystem
How can stakeholders trust the eSIM?
In the eSIM case, considering that a majority of mobile devices are hitting the market through open distribution channels, it is not feasible to rely on the expansion of contractual relationships between the device manufacturers and the operators. The situation will be become even more critical with expected development of connected devices and 5G use cases (IOT, industry 4.0, V2X, etc.) making the peer to peer relationships between stakeholders inefficient.
The first brick to cope with this new paradigm is to certify the different elements of the eSIM ecosystem: the eSIM production sites, the devices and the service platforms (like the SM-DP+). The GSMA eSIM specifications require for the eSIM a Common Criteria EAL4+, a globally recognized certification level commonly used for identity and payment services. In addition, the eSIM production sites and service platforms are GSMA SAS (Security Accreditation Scheme) accredited, which require the operational sites to pass a security audit ensuring that adequate security measures are in place to protect their assets.
The second brick consists of establishing a place where bilateral relationships (operators-SIM manufacturers) are replaced by multi-lateral exchanges between all eSIM stakeholders. This kind of organization, depicted in Figure 3 aims for a level of trust and security for eSIMs comparable to the one obtained with the state of the art SIMs cards.
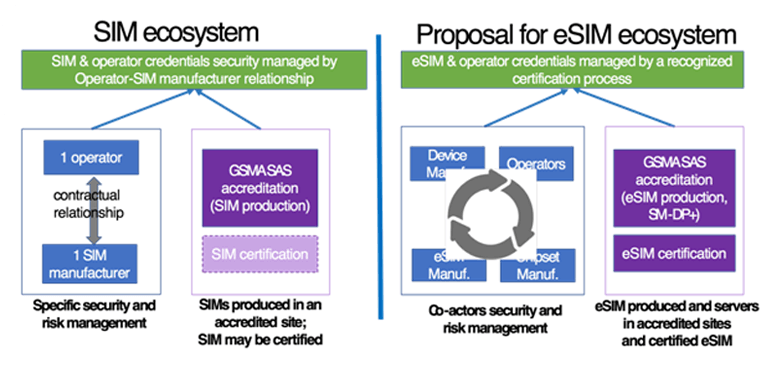
Figure 3: How to trust the eSIM as much as the SIM?
Security panel: role & relationship between stakeholders
As stated beforehand, the objective of the Security Panel is to replace the former bilateral operator/SIM-manufacturer relationship by bringing together all implied stakeholders such as operators, device manufacturers, eSIM manufacturers or service providers and by encouraging them to share relevant information, ensuring the emergence of an eSIM ecosystem trust model.
The Security Panel collects information and technical feedback about specific attacks and vulnerabilities from certification instances, for example the JHAS and other entities such as academics and it can issue, for example, informative reports (certificates status, security exposure, risk evaluation reports) to its members. The Security Panel has to be able to continuously monitor threats and security developments within the eSIM market and, additionally, has to be in charge of observing the eSIM products evaluation and certification processes.
Being aware of the security level of the various eSIM components through the Security Panel, operators and service providers can decide or not to install their profiles or services onto a particular type of eSIM, based on their own risk evaluations and relevant regulation.
The instantiation of this new role (Security Panel) in the various eSIM market segments is still to be studied. In particular, the legal status, obligations and responsibilities (individual and collective) of its members should be covered in different regulatory areas.
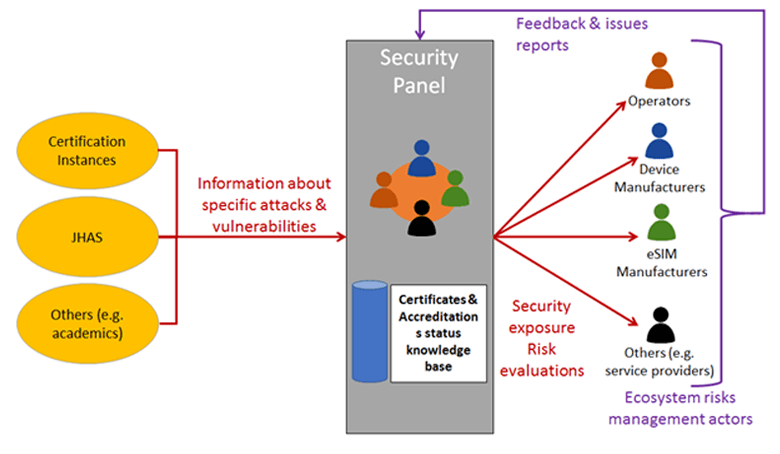
Figure 4: Security Panel’s objectives
Conclusion
The eSIM ecosystem involves numerous actors and requires more flexibility compared to the SIM ecosystem. At the same time, the security exposure will increase with the variety and the number of devices that will host an eSIM.
This shift in the ecosystem specifically challenges operators and service providers since they bear the same risks as in the SIM ecosystem while they have less visibility and control over the selected eSIM component. The device manufacturers are impacted as well, since from the instant the eSIM becomes an integrated piece within the device, a malfunction may affect the whole comportment of the device.
In this new situation, none of the stakeholders will be willing to take on the whole responsibility on its own. The model proposed in this article fosters the eSIM ecosystem stakeholders to be co-actors and co-responsible of the ecosystem’s global security. Its objective is to achieve the same level of trust by the eSIM as the one achieved by the SIM. For this purpose, the proposed model is based on the principles of certifying the different parts of the eSIM ecosystem and allowing each stakeholder to get access to security exposure and risk evaluations to use them in its own risk management and decision-making processes.
[1] “The SIM for the next Generation of Connected Consumer Devices”; www.gsma.com
[2] Subscriber Management Data Preparation
Related articles:
– eSIM
– eSIM: Coming soon to mobile networks and services near you!
– Orange at the heart of innovation with the new generation SIM card: the eSIM
– e-SIM supports and accelerates the development of IoT
Some definitions relevant to the eSIM ecosystem :
SAS certificate
The GSMA’s Security Accreditation Scheme (SAS) enables mobile operators to assess the security of their SIM and eSIM suppliers (SAS-UP : SAS for SIM and eSIM production), as well as the security of the SM-DP(+) platforms (SAS-SM : SAS for Subscription Management).
Device manufacturer
The device manufacturer integrates the eSIM provided by the eSIM manufacturer into the device and develops the adequate device interfaces to be compliant with specifications.
eSIM manufacturer
The eSIM manufacturer role is involved in the eSIM manufacturing and selling processes. It interacts with:
o the GSMA to obtain accredited certificate necessary to manufacture the eSIMs,
o the device manufacturer for providing the eSIMs.
GSMA
The GSMA is a body which supports and promotes mobile operators using 3GPP standards. It provides the functional and security requirements for the eSIM. The GSMA interacts with various actors of the ecosystem. It is responsible for conducting the SAS audits at SM-DP(+) and eSIM production sites. It manages the certificates of eSIM manufacturers and SM-DP(+) entities.
Operator
The operator provides a connectivity service to a mobile network. The operator has to interact with a SM-DP(+) entity for providing the data required for the profile generation and for authorizing the SM-DP(+) to generate and install the profile onto the eSIM.
Security Certification
Different additional entities are involved in the certification process of the eSIM (JHAS, evaluation laboratory, certification body, etc.).
SM-DP(+) (Subscription Manager Data Preparation)
The SM-DP(+) is a trusted role that (through a platform) prepares the profiles and install them securely onto the eSIMs. Whereas the SM-DP+ is related to the consumer market (e.g. smartphones), the SM-DP is related to the M2M market (e.g. connected cars). It has to interact with:
o the operator,
o the GSMA in order to get a valid SAS certificate which will be checked by the eSIM at the profile installation phase,
o the eSIM, verifying its eligibility during the profile installation phase, and checking the validity of the eSIM manufacturer certificate.