The PIN is dead, long live the PIN! Thanks to Artificial Intelligence (AI), your phone is now able to recognise your handwriting.
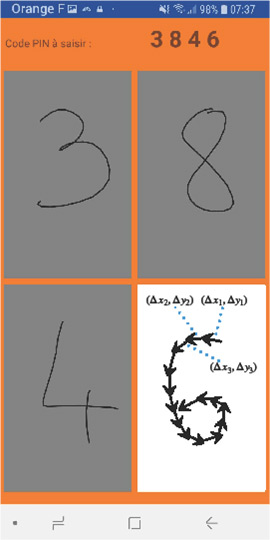
A new mobile app developed by a team of researchers from Rennes, France [1] will allow you to log in by writing on your smartphone. Replacing the famous virtual keyboard used for typing passwords, the app invites users to draw a 4-digit code with their finger to log in.
While graphology is a technique that has existed for centuries, recent work has shown that an AI is also able to recognise the author of a handwritten text by analysing their writing style [2]. Thanks to the computing power embedded in the latest generation of smartphones, it is now possible to perform this handwriting analysis based on only a few digits or drawings. Historically, AI has been used to recognise digits in images, such as automatically scanning postcodes or the amounts written on bank cheques, for example. Today, the machine is not only able to recognise digits, it can also recognise who wrote them.

The app in question does not use image recognition, rather it analyses the dynamics of the writing captured via the touch screen (speed, acceleration, curve, etc.). This is a form of “behavioural” biometrics [3] because it is based on analysing the user’s behaviour, i.e. the finger’s interaction with the screen. This form of biometrics has the merit of being much more difficult to imitate than physiological biometrics, such as facial recognition, where a simple photo can sometimes be enough to outsmart the system. To conduct this handwriting analysis, the application uses networks of so-called recurring neurons, which are tailored to processing sequences of variable length. In particular, they are widely used to understand natural language [4], in automatic translation systems or for the purposes of speech recognition, for example.
In the field of IT security, there are three different classes of authentication factor: memory factors (what I know), material factors (what I have) and biometric factors (what I am). Each factor class has its drawbacks: the risks of forgetting your password, the risk of losing your chip card, and privacy concerns for biometrics.
Nowadays, most systems are protected by one or two of these factor classes. For example, you usually access a bank website using a secret code (one factor: what I know), while payment by bank card generally involves two factors (the card I have and the secret code I know). Sometimes the secret code is sent by text message for online payments, although this method is now deemed unsafe: it is particularly vulnerable to “SIM swapping” attacks, where the hacker hijacks a phone number by registering it on a new SIM card [5].
The use of physiological biometrics became widespread on smartphones after the release of the iPhone 5S in 2013. Most terminals now offer facial or fingerprint recognition. However, the performance of these biometric systems has not been made public, and may vary greatly from one manufacturer to another (sometimes with colossal failures, such as the case of the Samsung S10 fingerprint sensor [6]). In addition, these biometric systems may simply be bypassed by entering a PIN. In fact, in the event that biometric recognition fails, the user is always given the option of entering a code. In terms of end-to-end security, the system’s security thus remains the PIN! As such, a malicious person will be more interested in stealing the PIN than duping the biometric sensor.
The handwriting recognition technology on offer is thus a means of securing PIN entry by adding a layer of behavioural biometrics. Should a malicious person steal your PIN, they will not be able to enter it, since the phone will fail to recognise their handwriting. Lastly, this is a more privacy-friendly approach to biometrics: via a privacy protection process known as “biohashing” [7], the representation of digits drawn by users is transformed into an irreversible imprint (it is not possible to recover the path using the imprint). This imprint is the only item to leave the terminal, and is used to validate authentication in the cloud (valid PIN and recognised handwriting). There is thus a reduced risk of hacking when it comes to handwriting, in contrast to facial or fingerprint recognition [8].
[1] SECURING SMARTPHONE HANDWRITTEN PIN CODESWITH RECURRENT NEURAL NETWORKS (pdf)
[2] Technical Correspondence (pdf)
[3] The password is you
[4] A word of innovation: NLP
[5] Qu’est-ce que le « SIM swapping », qui a permis de pirater le compte du patron de Twitter ?
[6] Le lecteur d’empreinte digitale des Galaxy S10 de Samsung trompé par un film protecteur
[7] Biohashing: two factor authentication featuring fingerprint data andtokenised random number (pdf)
[8] 27,8 millions de données touchées par une faille de sécurité chez un spécialiste du contrôle d’accès biométrique











