Long-lived confusions surrounding the Internet of Things have been compounded by the blooming buzz about the latest breed of “connected devices”. Uninformed or catch-all interpretations dilute the field into an “internet of everything”, while blinkered views narrow it down to one technology or network protocol. We try to sort out technical fact from hype by proposing a long-view and big-picture appraisal of this decade-old and still evolving field.
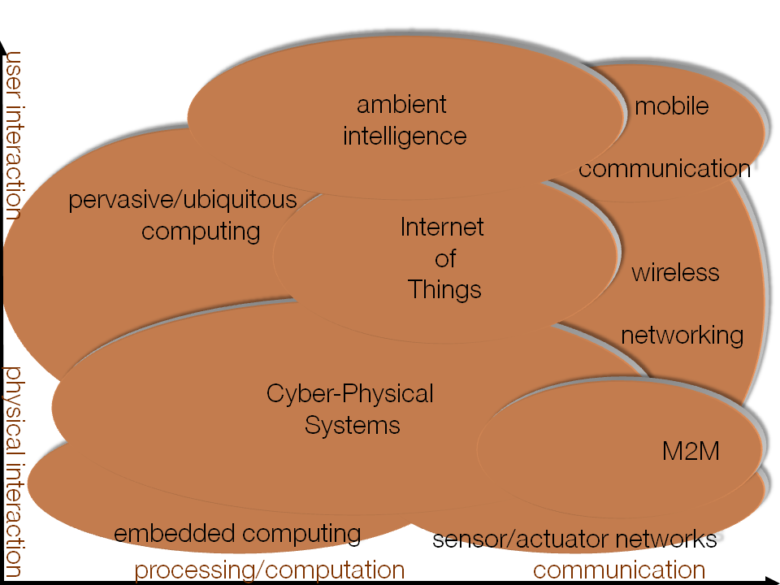
M2M/IoT/CPS topic map
The Internet of Things could just be, on the face of it, the latest technobabbly rendering of an evolution already captured by a confusing mishmash of earlier catchphrases: Smart Devices, Communicating Objects, Pervasive/Ubiquitous Computing, Ambient Intelligence, Machine to Machine (M2M), Cyber-Physical Systems. None of these hyped-up phrases are, at face value, equivalent, and each of them has been favored in turn by different proponents, communities and stakeholders, and tinted by their own biases and interests.
All of the misguided and obfuscatory views being bandied around through either of these buzzwords arise from failing to define the domain according to objective and long-lasting technical criteria. Moving away from this crowdsourced amalgamation of transient hype, we set things here in the perspective of the dual (and seemingly paradoxical) evolution of networks towards higher-level informational abstractions and their broader and deeper physical coupling.
From humans to devices, M2M in lieu of H2H
From the narrow vantage point of the telecommunications industry, M2M is still the preferred keyword, easily understood by exclusion as anything that is not human to human (H2H, i.e. interpersonal) or human to information (H2M, i.e. broadcast or retrieval) communication. In an even more blinkered view, M2M has tended to be implicitly limited by mobile operators to SIM-equipped devices, defined as M2M if they are not used for regular voice communication, or if communication is not their main usage. Beyond telcos’ purview, the Internet of Things has been gaining currency as a newer and more inclusive buzzword, but it has also tended to be restricted (at least implicitly) to either a dominant application sector (e.g. supply chain management) or a single technology (e.g. RFID). Before redefining it properly, we can provisionally take it as synonymous with M2M under an oft-repeated and all-too straightforward rationale: there are billions of devices and trillions of non-user-facing “things” out there, waiting in turn to get connected, whereas humans already are, through their regular communication-interface devices, supposedly. If some newfound variant of Metcalfe’s law were to apply, the promise of these upspringing connections would appear almost limitless.
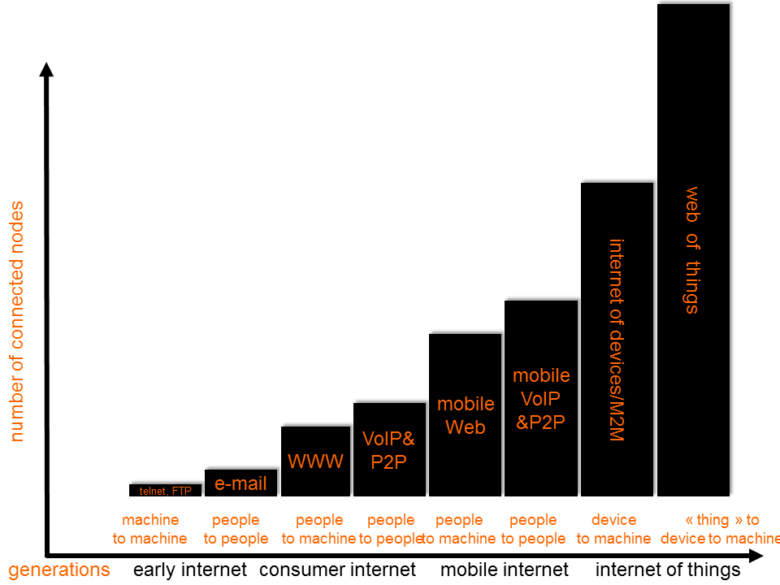
Successive stages of internet perimeter expansion (axes scales are not linear)
In a view that should not be taken too literally, humans are the bottleneck, not only for this promised population explosion of future networks, but also for their actual operation, as they are, compared to machines, hopelessly sluggish in both their data source and data sink roles. M2M bears the promise of liberating networks from this human bottleneck:-). According to a first defining criterion, no human user should thus be directly involved at either end of an M2M communication chain, nor should a person be “in the loop” of the real-time behavior of the system in which it is included. End users will not control or act upon this system under normal operating conditions, yet human operators may supervise or set parameters for the system, or retrieve information from it. The user interface used for these purposes by an M2M application is not considered part of the M2M system proper. This does also mean that the sensors and actuators of the M2M system proper exclude those that are used exclusively for direct regular human interfaces. Humans may be monitored by an M2M system, in which case they are considered to be part of the environment, and the sensors that monitor them are not human interface sensors such as used for direct explicit input from users by a regular human-facing application.
Yet this device-centric vision misses the crux of an evolution which is not only a quantitative extension of existing person-to-person and person-to-information networks, but a truly qualitative leap. For one thing, the internet was a machine to machine (in the sense of host to host) network before it became (indirectly) human to human, and it is only from the confines a parochial telco culture that M2M defined as “non H2H or non H2M” could be viewed as something new! This is why a key additional criterion is needed to distinguish the telcos’ M2M from the protohistoric host to host internet, or from present-day data base servers that synchronize their data, without any human intervention either.
As we have consistently asserted it since the early emergence of this field (refs 2-6), the second key criterion for an accurate technical definition characterizes an IoT/M2M system as involving distributed coupling between an Information & Communication System and the physical environment, supported by networked sensors and actuators.
From devices to things
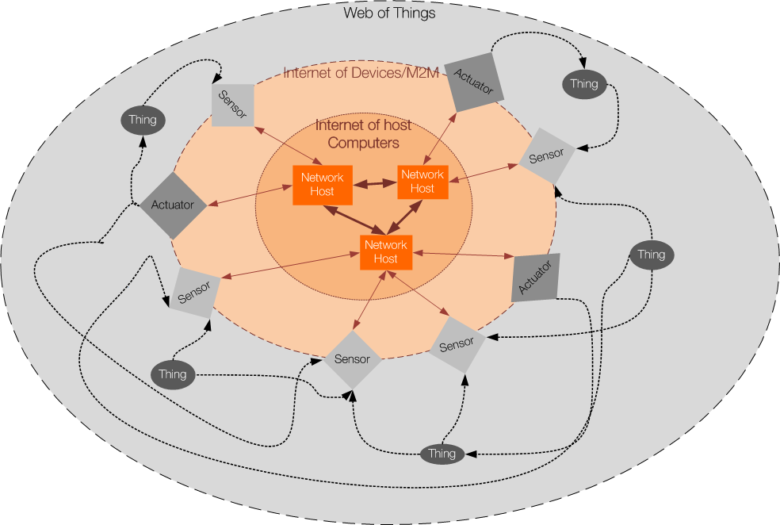
Nested perimeters of the Web of Things, the Internet of M2M Devices, and the core Internet
This first definition combining these two criteria (no humans in the loop & physical coupling) provisionally took IoT and M2M as equivalent. Differentiating them requires clearing up the meaning attached to “physical environment” vs. sensors and actuators in the second criterion.
In keeping with the literal nuance between “things” and “machines”, we may consider M2M to denote a more circumscribed vision of an “Internet of Devices”, where devices should be understood as network-connected sensors and actuators, or “machines” comprising these. According to our 2 criteria, devices/machines that are used exclusively for information processing, storage and communication (such as e.g. servers or routers), or for which sensors and actuators are used exclusively to support regular human interfaces, such as smartphones, should not be counted in for M2M or IoT proper. The hype about the newer breed of “connected devices” has, just as the earlier “communicating objects” of the early 2000s, muddied the picture by implicitly lumping together all species of networked devices. The devices that make up M2M systems and the Internet of Devices in this strict and proper sense are networked sensors, actuators, or more generally networked “machines” or appliances equipped with physical transduction (sensing & actuation) capabilities that correspond to their primary function, communication being only an added functionality. They are, in a proper sense, “embedded” in their physical environment, adding information acquisition, processing, transmission and actuation capabilities to this environment.
Beyond these devices, the Internet of Things may, in its extended acceptation, reach further to integrate, in its outermost layer (see diagram above), all kinds of actual physical items that are not devices connected to networks. These have traditionally been items equipped with RFID tags in classical supply chain or inventory management applications, but neither the use of radio technology nor universal identification is actually a prerequisite for this. Tags, be they radio-frequency or optical, may be dispensed with altogether if things may be “recognized”, tracked and identified through a combination of available sensors in at least a given environment. This kind of analog (or, more accurately, “phenotropic” [3]) interface is “thing-friendly” in the same sense as a user-friendly interface adapts to the user rather than requirinng him to adapt to it. Target “things” that may thus get integrated on their own terms may be legacy home appliances, pieces of furniture or industrial machinery, rooms or other subsets of space. Encompassing as “things” both familiar graspable objects and entities of space re-unites the two strands of research that, originating from pervasive computing, had tended to separate under the Internet of Things and Smart Spaces/Smart Environments.
Connecting these “things” and other physical entities that are deeply embedded in the physical environment and have their own non-informational role in this environment, opens up entire new application domains such as supply chains, transportation or energy networks, that were so far outside the purview of state of the art ICT, or for which information systems were disconnected from the corresponding physical processes, requiring manual configuration and manual data entry by an operator to couple the two. Again this may extend beyond tag-based inventory and supply-chain management by relaxing the constraint of prior identification in a single universal identification and naming scheme.
From interactive to reactive
The idiosyncratic requirements of future M2M and IoT applications stem directly from these definitions: because the underlying systems are strongly coupled with their physical environments, applications inherit the specific physical constraints of these environments, which differ markedly from those of human-facing interactive ICT services. By contrast, environment-facing reactive systems are bound to react deterministically to events originating from the environment.
Cyber-Physical Systems (CPS) specify the previous definitions further by placing emphasis on the automatic control dimension (“cyber” in the original sense) and thus on bidirectional coupling between distributed ICT systems (“cyber” in the 1990s sense) and physical systems, for joint monitoring (through sensors) and control (through actuators) of this physical system through a network. Contrary to user-centric interactive ICT systems that may respond at their own speed in a best-effort way, environment-centric reactive CP systems must react at a speed imposed by the environment, at least within fixed latency bounds. Networked CPS may draw for this upon a vast body of embedded and real-time computing know-how, applying it in a new way to large-scale networks, non custom-designed or even self-configurable systems.
From applications to systems
Rather than isolated M2M/IoT applications or services, the target of design should be comprehensive M2M/iOT/CPS systems, as emphasized in the previous definitions. For this, we have to get past the narrowly functional views that still prevail (at least implicitly) in the software industry, whose design paradigms have been widely adopted by the telecom industry. M2M/IoT/CPS systems are meant to support such applications and services, but they should be designed holistically as systems, accounting for all overt and hidden interactions with their environment.
Way beyond present-day bread-and-butter M2M/IoT applications, which mostly boil down to vertically integrated remote monitoring & data acquisition from sensors, a shared multilayered infrastructure [1] providing bidirectional coupling between IT systems and physical environments, over multiple scales and abstrraction levels, portends the future of the IoT when it gets integrated into cyber-physical systems in the proper sense. Besides this “horizontalized” architecture, the design of IoT systems in their evolution to CPS needs to borrow from control theory, real-time embedded systems and, ultimately, robotics. They are also prototypical “systems of systems” and cannot as such be the object of a 100% top-down engineering: they need to accommodate bottom-up growth and to integrate self-configuration and self-healing properties, drawing for this on the complex graph of physical interactions that captures the intricacy of their physical grounding.
…and back to humans
The original web has been moving one (huge) step up from connecting computers by cables (as the underlying internet did) to connecting documents (hosted by these computers) through hyperlinks. Understanding the Internet of Things in the sense proposed here is just as huge a qualitative step, from connecting devices to connecting things interfaced through these devices. This is the most relevant analogy to understand what is achieved by moving from the Internet of Devices to the Internet of Things, or, more pointedly, to the Web of Things. The Web of Things has been understood so far as the application of (REST) architecture principles derived from the web to the internet of Things, but it will ultimately converge to the evolution of the web itself towards both the web of data and the semantic web, which Tim Berners-Lee had from the very beginning envisaged as destined to encompass all physical things: “In the next step, the Semantic Web will break out of the virtual realm and extend into our physical world”. This is, crucially, more than a perimeter extension, it is a quantum leap in the way we define the nodes of the relevant network, moving away from network protocols to identifiers that link directly to all relevant semantic information to support their interpretation at all relevant levels of abstraction. This interpretation is intended for machines to process automatically without any “out of band” information, but it does also, not incidentally, raise the network much closer to what is actually relevant for human users, thus making the “thing-friendly” IoT also “user-friendly”! From a low-level network viewpoint, the “things” of the web of things may appear as high-level abstractions, but they are actually those that matter to humans, the very same they perceive and reconstruct through their senses, the ones infants make sense of by touching, grasping and acting upon them.
Abstracting devices away is, of course, nothing new in the realm of social networks, which have long since done this by massively interlinking humans and identifying them directly as persons rather than through the addresses of their computers or devices. Ultimately, rather than through an all-confusing “internet of everything”, the relevant level at which existing information networks, social networks, and the web of things will be jointly subsumed may be what Tim Berners-Lee has deservedly dubbed the “Giant Global Graph”, an ethereal abstract network that will unitedly encompass data &information items, physical things and persons as its nodes. The “internet” moniker is but a lame and anachronistic metonymy for this all-embracing graph, for which future avatars of IP as we know it would be just one deeply hidden layer of a multilayered distributed infrastructure, united at the top, and closer to us, by shared semantics.
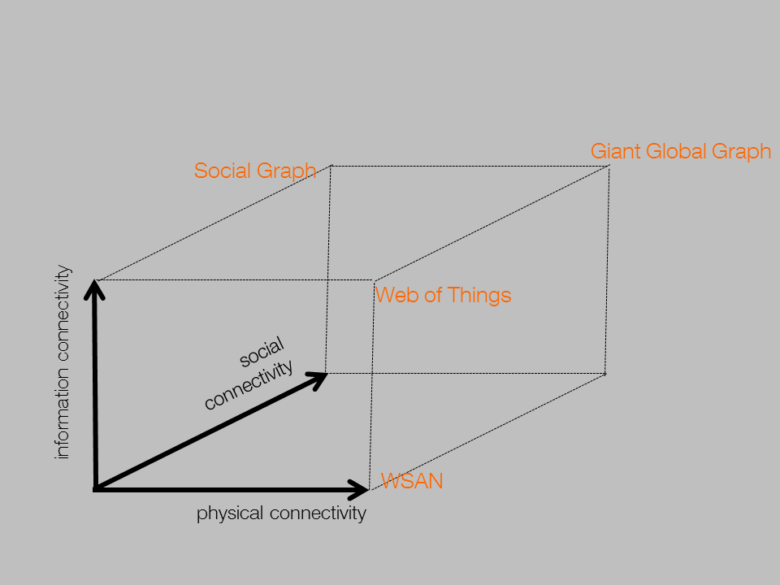
Conjoining 3 dimensions of connectivity