“By making the invisible visible, the nutritional or environmental benefits of products are improved. The same applies to security.”
A Complex Ecosystem with a Multitude of Concurrent Radio Frequency Technologies
By the end of the year, 12 billion objects are expected to be connected to networks, and that figure is expected to rise to 27 billion [1] by 2025. Most of these devices are connected to the Internet through wireless technologies. However, slightly less tech-savvy readers may be surprised to learn that there are not just one or two main wireless protocols but a whole sea of options. Manufacturers make their choice based on criteria such as range, throughput, power consumption, security and cost. For example, some objects use long-range technologies such as 4G and 5G cellular networks or LoRaWAN. Other devices use Wi-Fi, Bluetooth or lesser-known protocols such as Z-Wave, ZigBee, DECT Ultra Low Energy and, in the future, Thread and Matter. This diversity of radio frequency technologies, and their multiple configuration options, is a weak spot in terms of security.
Weak Security, Particularly with Radio Waves
Unfortunately, security is not yet a priority for many manufacturers. Not all security specifications are typically implemented on the grounds of costs. Too many objects have hardware weaknesses (open debug ports), software weaknesses (remote hijacking or malware being installed) and radio wave vulnerabilities. Researchers in the field of security regularly show that even mature technologies such as Wi-Fi or Bluetooth are affected (for example FragAttacks [2] in 2020 and BrakTooth [3] in 2021). These vulnerabilities affect the biggest names in the industry and can lead to considerable consequences for customers, such as their Wi-Fi password being stolen. The fact that they can be exploited remotely without a trace makes these vulnerabilities all the more significant. For example, anyone on the street with a vehicle and the right equipment can attempt to access information or carry out intrusion and denial-of-service cyber-attacks.
Good Security Practices Are Necessary but Not Enough
Orange is actively working with standardization bodies to put forward proposals of European security certification schemes, for example, the ETSI EN 303 645 standard: “Cyber Security for Consumer Internet of Things: Baseline Requirements.” This approach is necessary, but it is not enough. The choices made during a product’s design phase are based on an up-to-date freeze-frame of best practices. However, vulnerabilities are frequently discovered after a product has already been rolled out. Furthermore, the overall security level of a service depends not only on the object, but on a set of factors such as the security of other devices and platforms with which it exchanges data, the place of installation (in a public space or not) or the behavior of the end user (e.g. setting a weak password).
A Diagnostic and Monitoring Tool for Nearby Radio Activity
Radio scanning applications are already available on smartphones to help users assess the level of security on their device. However, these are restricted by hardware constraints and permissions granted by the operating system. As a result, the innovation involves developing and patenting a smart radio wave scanner. The scanner has multiple antennas to handle a wide range of radio wave technologies. Unlike a smartphone, it can pick up background radio traffic that it is not intended to receive. Finally, it can simultaneously track communications on several frequencies.
The scanner uses open-source software that Orange has actively contributed to, such as Kismet [4], a Wi-Fi probe. It also integrates components developed by Orange such as a Bluetooth analysis module or the visualization interface. The scanner is currently a single-purpose object. However, some or all its hardware and software components could be integrated into a future iteration of the Livebox.
At Orange’s 2021 Research Exhibition [5], three use cases were demonstrated. The first involves detecting and characterizing devices within radio range (at home or close by). This allows users to locate Wi-Fi access points with weak levels of security or objects emitting radio waves without their knowledge. The scanner can do more than smartphone applications. This is because it can identify clients connected to each of the nearby Wi-Fi access points and the volumes of data being exchanged. It can also detect Zigbee-connected objects such as connected light bulbs.
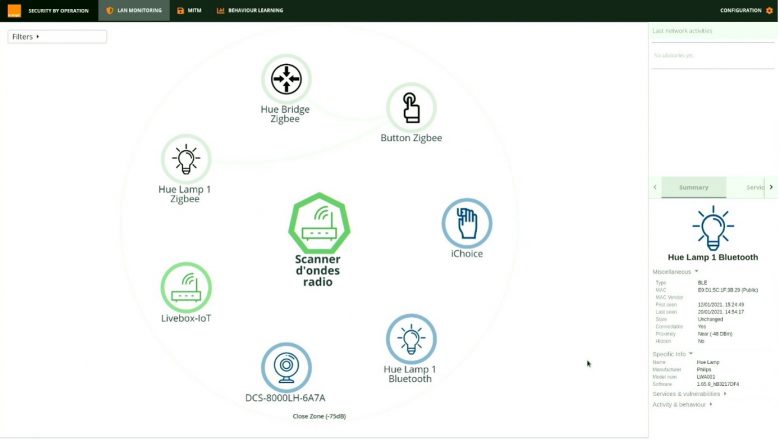
Figure 1: Wi-Fi, Bluetooth and Zigbee objects within the scanner’s radio range
In the second scenario, the scanner detects if sensitive data could be compromised by passive eavesdropping of radio-wave. This could be health-related data or confidential information such as a Livebox Wi-Fi password. This happens by monitoring objects at the right time, such as after they are connected. The scanner then analyzes whether the data is transmitted unencrypted [6] or if it is poorly protected, as is the case with some connected cameras [7].
Finally, the last use case involves detecting attacks that can be carried out by a malicious person in close vicinity or a burglar wanting to disconnect an object such as a surveillance camera. To do this, the scanner monitors background radio traffic and identifies the active exploitation of known weaknesses in wireless technologies. These vulnerabilities could lead to an object being forcibly disconnected from its Wi-Fi access point due to the mass sending of spoofed signals [8] or the creation of an evil twin [9].
An Innovation to Make the Invisible Visible
This innovation is particularly promising in the workplace. One or more well-placed radio scanners can trigger alerts based on rules defined by a site security manager. It gives the ability to identify threats coming from vulnerable personal objects of employees or visitors, which could lead to intrusions into the information system via unmonitored radio communications. A security score can also be generated to draw up a list of authorized devices in a given geographical area. It is never easy to grade equipment, especially when the grade is bad. Any reluctance to do so must be overcome, however this type of resistance is not specific to the security sector. Similar questions slowed down the development of food and energy labeling. Yet today, labels and applications indicate whether a product is good or bad for the health and the environment. By making the invisible visible, the nutritional or environmental benefits of products are improved. The same applies to security. To increase security, we need to improve user awareness to push the market to do better.
The scanner is a well-suited tool to monitor connected objects. It performs better than smartphone applications, which are restricted by hardware constraints and permissions granted by the operating system. It detects nearby vulnerable devices, data that could be compromised during communications, as well as radio-wave attacks. It helps users to be aware of risks and threats. It provides a means to gain more control over nearby radio activity.
[1] https://iot-analytics.com/product/state-of-iot-summer-2021
[2] https://www.fragattacks.com
[3] https://asset-group.github.io/disclosures/braktooth
[4] https://www.kismetwireless.net
[5] https://mastermedia.orange-business.com/p?t=mymuQL1DU#/share/media
[6] https://github.com/bmork/defogger
[8] http://users.csc.calpoly.edu/~bellardo/pubs/usenix-sec03-80211dos-html/aio.html
[9] https://ieeexplore.ieee.org/document/9398377








