Summary
“Quantum physics as a solution for securing future communication” – Orange is involved in the operational and research challenges of Université Côte d’Azur’s Quantum@UCA project on quantum cryptographic key exchange over a city network. An experimentation agreement has just been signed between the two entities according to which Orange will both provide “dark fibre” for the exchange of quantum states and lend its expertise in cryptography. Through its Quantum Photonics & Information Team, Université Côte d’Azur will provide its own expertise in the field of engineering and quantum photonics technologies. The ultimate goal is to implement a complete secure channel system based on quantum physics.
Full Article
Cryptography has been used to protect data for several millennia, whether to ensure confidentiality, integrity or authenticity. Nowadays, it is based on the definition of algorithms which are themselves considered to be in the public domain, using one or more cryptographic keys which must remain secret in order to ensure the security of the overall system. In the case of so-called secret-key cryptography, which is the focus of this article, there is one “secret” key shared between the various authorised entities. As such, it is first necessary for those parties to be able to share it in a secret manner. For the sake of completeness, modern cryptography also provides solutions to this issue of key agreement/exchange. The best-known method is that proposed by Whitfield Diffie and Martin Hellman during the 1970s, which is today widely used in e.g., web browsers. It is based on the mathematical difficulty of computing a discrete logarithm using sufficiently large numbers (e.g., 256 bits).
While there is no doubt that the currently deployed cryptographic algorithms are perfectly secure today, it is important to remain vigilant about the threats that may arise in the future, particularly those related to the emergence of quantum computers. Indeed, it is already well known that such computers would be capable of breaking a whole range of current cryptography, including the Diffie-Hellman key exchange but also that of other systems that are currently used on a daily basis, such as in internet browsing or banking transactions!
Although these higher capacity computers are not yet available, the risk is so high that it is important to find alternatives to these cryptographic mechanisms used every day.
It turns out that these alternatives already exist and research in cryptography has been working on it for several decades. More specifically, two slightly different approaches have been developed to date. The first, commonly referred to as “post-quantum cryptography”, is based on mathematical problems that are different from those used today. The second approach is very different and itself relies on quantum physics to propose new cryptographic solutions. It is the approach that is the subject of the partnership just signed between Orange and Université Côte d’Azur (UCA) via the Quantum@UCA project integrated within UCA’s IDEX initiative, described below.
Quantum key exchange
The initial idea for so-called quantum cryptography arose from the work of Charles Bennett and Gilles Brassard during the 1980s. It is based on the “quantum non-cloning“ principle which states that it is impossible to create an exact replica of an unknown quantum state. Let us suppose that two partners, Alice and Bob, want to create and share the same cryptographic key. In Quantum Key Distribution, Alice will initially select a key at random and send it to Bob bit by bit. In order for this transfer to be carried out securely, Alice and Bob will share quantum states (qubits), at a rate of one per secret key bit. More specifically (see also Figure 1), the various steps for establishing the key are as follows:
1. Alice randomly generates, for example n bits, and some of which will form the key that is eventually shared;
2. Alice chooses n bases for the emission of each photon (one photon per exchanged bit);
3. Alice sends one polarised photon per bit of the key, depending on the generated bit and the selected basis, and sends the photon to Bob;
4. Bob also chooses n bases to receive the photons;
5. Bob receives the n polarised photons based on what was sent by Alice, and on the basis that he has chosen.
6. Finally, Alice and Bob compare the bases they have chosen. If they are identical, the bit is retained for the key, otherwise it is rejected.
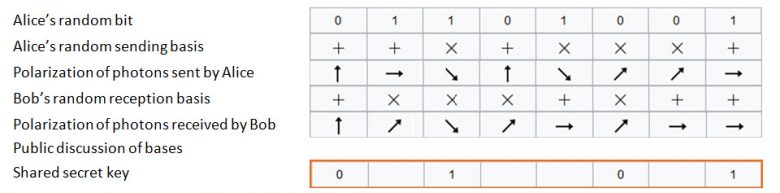
Figure 1: Bennett and Brassard Quantum Key Exchange.
If an external attacker not knowing the used quantum states tries to intercept certain photons sent by Alice, it would inevitably be detected by Alice and Bob (due to quantum non-cloning), allowing them to exclude the corrupted bits from the key that is eventually shared. Security is no longer mathematical but based on the basic principles of quantum physics and is considered theoretically (or unconditionally) “perfect”.
Securing the exchange
Once the key has been securely established between Alice and Bob, the two parties can then use it to secure their exchanges in terms of confidentiality and integrity.
However, there is one essential condition in order for the whole process to work securely: it must be possible for Alice and Bob to be able to authenticate each other via another channel. Without this, the attacker could impersonate Bob to Alice during the execution of the quantum key distribution, and eventually recover the secret key.
However, quantum cryptography does not yet have a solution for the last two points (protection of future communications and creation of an authenticated channel). It is therefore necessary to use traditional secret-key cryptography mechanisms, bearing in mind that the unconditional security provided by quantum key exchange is also achievable through conventional systems such as the “one-time pad” for confidentiality or the Wegman and Carter authentication code for integrity. The use of a system such as AES would diminish the obtained theoretical security.
The Quantum@UCA project at Université Côte d’Azur
Photonics is required to play a major role in the practical implementation of this quantum key exchange. At first, the quantum properties of photons are today all fully mastered at a fundamental level, which is essential for studying them in theoretical terms and understanding how they change in a restricted environment (terrestrial fibre optic link or satellite link in open space). In addition, all the technology used to efficiently generate and manipulate photons in a coherent and individual way is now very mature. It is therefore entirely possible to work on single or entangled photons, for example by using integrated-optics components, ensuring the implementation of stable, high-performance systems that are capable of leaving research laboratory to go into a real-world deployment. They can also be sent over long distances using low-loss optical fibre and dedicated high-performance fibre components. They are therefore all suitable for carrying out the practical implementation of secret keys between different partners.

However, several fundamental and technological constraints limit the current performance of quantum cryptography. The first constraint concerns the potential throughput, which is currently very low, for establishing the keys. The second relates to the potential distance between Alice and Bob. The Quantum@UCA project will primarily focus on the first item. In order to do so, it will be based on the problems of non-ideal photon number data (in order to have only unique and therefore “useful” photons), unoptimised error correction codes (to correct errors), and detector noise (to limit “natural” loss, not due to an attacker).
In practice, the exchange of photons will be performed using high-quality bipartite frequency comb-type entangled photonic states, coded using discrete or continuous variables. The photons will be generated on telecommunication wavelengths from a central node located on the Nice-La-Plaine-du-Var campus. They will then be distributed on different two-node fibre optic links to two different nodes located on the SophiaTech and Nice-Valrose campuses.
The main idea of the project is to test, improve and validate on the spot all strategies and ideas that have been imagined or tested in the laboratory so far, or to find new approaches to improving the actual throughput. It will also be a question of using various quantum secret key extraction protocols in order to guarantee the highest level of data exchange confidentiality while effectively responding to the various envisaged use cases. The Université de Côte d’Azur teams are at the forefront of research on those aspects, and will be at the heart of the project’s photonic-related research.
Contribution of Orange
The contribution made by Orange is two-fold. From an operational point of view, Orange has provided two strands of dark fibre between Sophia Antipolis (INRIA) and Valrose (INPHYNI), with an access point on the Plaine-du-Var campus (IMREDD). This fibre aims at enabling the exchange of photons, and therefore quantum states, between “Alice” and “Bob”. From a research point of view, Orange will provide its expertise on cryptography, by working on the most appropriate cryptographic algorithms that will be used for setting up the authenticated channel and for providing communication confidentiality and integrity once the key has been shared between the network points. The scientific thoughts will also focus on the other uses of quantum cryptography, which may go beyond key exchange and that can be implemented between the three points of the quantum network. The implementation of a complete system enabling firstly the exchange of a cryptographic key and then its use to ensure the “perfect” confidentiality and integrity of the data sent is the intended outcome of the two partners.
Conclusion
On a strategic level, it is of the utmost importance that French initiatives should be able to launch efforts to work on secure communications networks and quantum detection. In this regard, this agreement between Orange and Université Côte d’Azur, in conjunction with the Quantum@UCA project, represents a unique experimentation opportunity to implement, for the first time in France, a quantum communication platform that can be used for research, for special awareness events, or even for entrepreneurial activities.











