
Data protection and security on softwarized infrastructures continue to pose major challenges, including introspection, system isolation and supply chains. With public clouds becoming increasingly popular, how can it be ensured that they provide the same level of protection as private or on-premise clouds, which tend to be more secure?
The security potential of TEEs remains largely unrealized despite the fact that hyperscalers are adopting them. TEEs could become the future of security.
This is one of the many applications of TEEs, or Trusted Execution Environments. TEEs are a central component of confidential computing. Quite simply, this involves services and data being protected without the infrastructure provider having to be trusted. IBM has gone so far as to describe confidential computing as the “next frontier in security” (*). Gartner deems the related privacy-enhancing computation techniques to be one of the top security trends to watch out for.
TEEs may be seen as a hardware-secured “safe” designed to protect service execution and provide strong security-related assurances in terms of data and code confidentiality, integrity and isolation. This technological breakthrough is primarily derived from cloud computing. But what are the opportunities and risks for telecoms carriers?
A research study carried out by Orange in 2022 assesses the security-related impact of TEEs for telecoms. This study was carried out in the Trust, Security and Transactions research domain together with TAGES SolidShield, a partner of the EU-funded INSPIRE-5Gplus project, and its findings have recently been published in the IEEE Security & Privacy international journal following a thorough selection process under the coordination of Pennsylvania State University [1] – only seven articles were selected for this special issue on the impact of emerging hardware on security and privacy. The Associate Editor-in-Chief of IEEE Security & Privacy has been providing key contributions to systems security, particularly concerning SELinux, for more than three decades.
The opportunities and risks of TEEs are comprehensively analyzed using the SWOT (Strengths, Weaknesses, Opportunities and Threats) approach. This provides an overview of: (1) the strengths of a security technology for protecting critical assets, and (2) the main applications; but also its possible limitations in terms of (1) residual threats, and (2) barriers to uptake.
The study’s findings suggest that TEE security has strong potential for Orange.
TEE Overview
TEEs provide security through their hardware root of trust embedded in the main processor to create isolated execution environments called enclaves, cryptographic protocols for memory integrity and confidentiality, and services such as attestation.
As Figure 1 shows, a malicious system layer, hostile co-located processes, and introspection of application data from lower layers are the main attack vectors on the TEE. The study compares confidential computing solutions based on the isolation, memory protection and dynamic migration they provide.
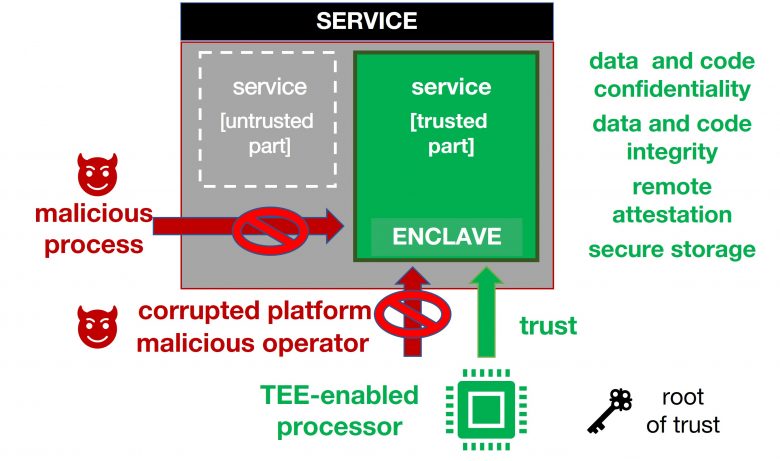
Figure 1: TEE — overview, attack vectors, and security guarantees
The TCB (trusted computing base) of a TEE architecture is highly flexible, which makes it easier to support multiple applications. These applications can include protecting against the infrastructure to ensure that virtualized cloud or network functions are secure, automating network security, and protecting distributed applications or artificial intelligence systems in terms of models or data. While process-based solutions (Intel SGX) have a minimal TCB that is more secure, they are not as intuitive as virtual machine-based solutions (Intel TDX, AMD SEV), which have a more extensive TCB but are easier to use.
TEE functions are implemented in hardware but sometimes also in software, by virtualizing the TEE such as in a virtual machine instance. Virtual TEEs have the benefit of being relatively simple to use and maintain, albeit at the expense of security.
TEE Applications
Cloud and mobile are the two categories of application of TEEs. Cloud applications are more varied and involve more established technology.
- For the Cloud
The relevant applications here are those related to confidential computing, such as healthcare (e.g., data protection across multiple hospitals), telecoms infrastructures and 5G verticals (e.g., connected vehicles), financial applications, and AI. The ecosystem is dominated by hyperscalers (e.g., Microsoft, Google, Amazon) using the key technologies of Intel SGX to protect processes and Intel TDX and AMD SEV to protect virtual machines.
Applications under a first category aim to protect cloud functions against introspection of application data by the cloud provider (securing virtualized network functions). For example: for 5G networks and the IoT-cloud continuum: trustable base stations, supply chain security using user-centric RISC-V enclaves, network security monitoring.
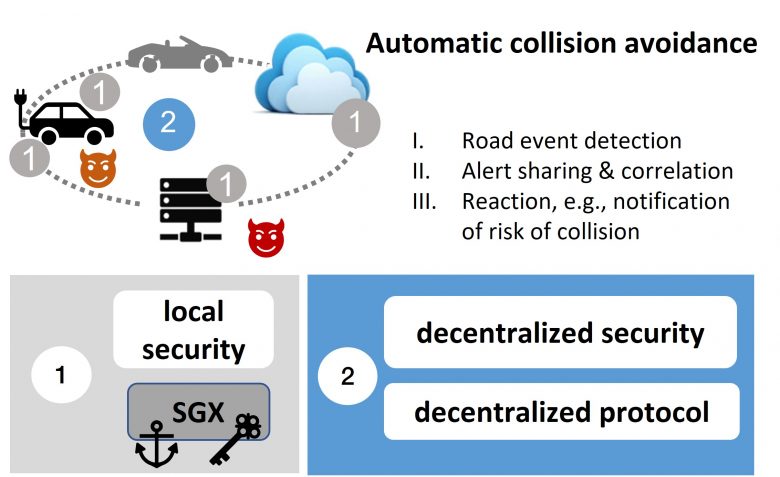
Figure 2: TEE for securing distributed applications — early collision detection for connected and autonomous vehicle networks
Distributed applications in an untrusted heterogeneous environment fall under a second category. These applications include: protecting data for early detection of collisions between connected vehicles (5GCroCo EU-funded project), isolation of vehicle functions, secure orchestration of native cloud functions, or “confidential” managed services.
Figure 2 shows how a TEE is used to prevent collisions in autonomous vehicle networks, combining the high local level of data protection provided by the TEE with more flexible decentralized security using a distributed protocol.
A third category of application focuses on AI security (confidential machine learning) to protect user data and learning models. For example: distributed, privacy-preserving AI — these approaches have also been explored by other carriers such as Telefónica and by startups.
- For Mobile Environments
The objective is to offer protection against a multitude of hardware attacks on IoT devices. TEEs now provide security for traditional applications based on hardware credentials (HSMs, TPMs, smartcards), including ticketing, device/user authentication/identification, access control, and extending applications to new scenarios (e.g., BYOD).
This ecosystem is dominated by ARM TrustZone hardware isolation technology for the development of secure applications (Trusted Apps) and by the Global Platform standard. However, this ecosystem is not open-source, which prevents Trusted Apps from being installed on mobile devices. Carrier-centric approaches are promising, using the box to control the installation and deployment of authorized Trusted Apps without getting the mobile platform provider involved.
Malware prevention of code injection attacks is a key application. ARM TrustZone provides protection by authenticating pointers before or after a jump instruction.
SWOT: TEE Opportunities and Risks
A SWOT analysis helps identify the strengths, weaknesses, opportunities and barriers to uptake of TEEs in order to conclusively address whether a TEE is capable of providing security in a telecom environment.
Figure 3 provides an overview of the SWOT analysis performed. Below, we examine the main points.
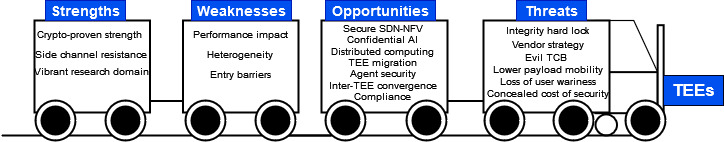
Figure 3: TEE SWOT analysis overview (strengths, weaknesses, opportunities and threats)
The first strength to mention are the strong security assurances due to hardware protection. The TEE ecosystem is highly dynamic with many frameworks to ease implementation and interoperability of heterogeneous technologies (e.g., Confidential Computing Consortium). TEEs are also pivotal to the confidential computing strategy pursued by major cloud providers (Amazon, Microsoft, Google). Lastly, these technologies are flexible enough to respond to new threats (e.g., side channels) using firmware updates.
On the weakness side, TEEs require to find delicate trade-offs between security and performance: limitations on the size of the TCB, and additional costs incurred as a result of execution context switching across enclave boundaries and due to data encryption. Interoperability is another major hurdle, with multiple heterogeneity barriers (applications, hardware architectures, security technologies). The TEEs integrated in the cloud platforms are making it easier to overcome these challenges, although they do remain an issue.
As for opportunities, the applications mentioned previously notwithstanding, TEEs show great promise for maintaining security when devices or networks are migrated within the IoT-cloud environment. Secure and transparent migration during execution of cloud payloads remains a challenge due to the difficulties of managing the security context. To protect data in complex, externalized regulatory settings (GDPR, NIS2, extraterritorial laws), TEEs also prove useful in security-by-design and privacy-by-design approaches.
Lastly, in terms of threats, although a great number of side-channel attacks have been reported, their significance must be put into context for the telecom environment. The attacks are based on assumptions (e.g., co-location of the attacker and victim, malicious kernel, knowledge of the victim’s code) that can be overcome by applying ETSI recommendations.
Among other attacks, some of the most significant continue to be denial-of-service attacks (e.g., Rowhammer memory “bit flipping”), caused by an overly inflexible integrity policy. Malicious use of a TEE in a trusted infrastructure to conceal malware with total impunity is an issue that still exists. It is particularly difficult to mitigate these highly targeted attacks at a reasonable cost. From the perspective of business and to remain competitive, partially discontinuing a TEE technology has a clear impact on the migration of technology for customers and may cast doubt on investments made. A recent example of this is the switch from Intel SGX to Intel TDX.
Outlook
The bottom line is that the benefits far outweigh the risks for the telecom industry. Fundamentally speaking, TEEs continue to be highly robust and are seldom the subject of genuine attacks. The TEE ecosystem is highly dynamic, supported by major cloud operators, with flexible technologies. The barriers identified are diminishing, and the number of opportunities is high and rapidly increasing. With automation on the rise, operators could be tempted to embrace larger TCBs that encrypt full VMs, but which may also be more vulnerable. Attacks, and especially denial-of-service attacks, are of course something that must continue to be monitored. Looking beyond the technology, regulatory aspects (e.g., GDPR, NIS2, sovereign clouds) must also be considered.
The security potential of TEE technologies is still largely unrealized despite the fact that hyperscalers are extensively adopting them in their industrial cloud platforms. It is therefore vital to raise widespread awareness of TEEs and to make decision-makers more familiar with them.
These technologies have reached a certain level of maturity. What will happen in a decade’s time? IBM’s prediction may well come to pass with TEEs becoming the future of security (for cloud, and elsewhere) and being deployed much more widely, with new applications. These emerging technologies therefore need to be considered within a global security roadmap for a carrier such as Orange.
The future is bright, and new challenges lie ahead for Orange’s research!
(*) Confidential computing as the “next frontier in security” :
This joint statement from a number of Vice Presidents and the CTO of IBM Cloud sheds light on IBM’s confidential computing vision and recent activities. IBM now joins the group of hyperscalers that includes Microsoft, Amazon and Google, becoming a major force in this sector. The consensus for confidential computing being the “next frontier” for data protection was recognized in an Everest Group study.
Sources :
- Marc Lacoste and Vincent Lefebvre, Trusted Execution Environments for Telecoms: Strengths, Weaknesses, Opportunities, and Threats, in IEEE Security & Privacy, special issue on Impact of Emerging Hardware on Security and Privacy, vol. 21, no. 3, pp. 37-46, May-June 2023, doi: 10.1109/MSEC.2023.3259801.
Read more :
- SWOT analysis:
- HTML version: https://ieeexplore.ieee.org/document/10098483
- PDF version: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=10098483
- « Special Issue» IEEE Security & Privacy on hardware security: https://ieeexplore.ieee.org/stamp/stamp.jsp?isnumber=10137354








