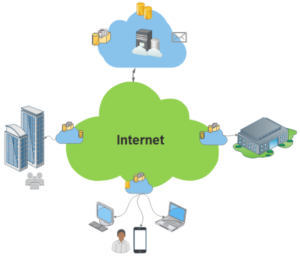
Figure1: Decentralized architecture
Novel decentralized cloud architectures (Figure 1) extend traditional clouds beyond core data centers by migrating virtualized resources to the network edge. Such architectures are particularly interesting for Internet of Things (IoT) applications generating high volumes of data that require significant resources for processing. All cloud architectures, old and new, leverage virtualization technologies, which have an impact on security.
The Isolation Challenge
Virtualization achieves isolation between virtual machines of different users by partitioning resources of the underlying physical machine. However, such partitioning is challenging: sharing physical resources between multiple virtual instances may result in information leakage between them through side-channels. It means leaking secrets outside regular communication channels/interfaces. These channels are created by mechanisms found either in the virtualization layer or in the hardware layer. For instance: in the virtualization layer, memory deduplication improves memory performance [1]; in the hardware layer, one key shared resource is the processor that may leak information through its cache architecture. These channels may be exploited by an adversary through side-channel attacks.
Side-channel attacks have an old history. There are different categories of attacks according to the type of exploited channel: timing, cache-based,electromagnetic, and power analysis attacks. Electromagnetic and power-analysis attacks are more applicable to physical devices such as smartcards. As an example of the timing attack, during the execution of a cryptographic algorithm such as RSA, the multiplication operation takes different timing values than the other operations (Figure 2). Therefore, an adversary may exploit this time difference to distinguish between different operations executed during the encryption process, and to retrieve the encryption key by estimating bits of the key. The same scenario is applicable for power analysis attacks, i.e., the attacker identifies the operation that consumes more power than others to retrieve information.
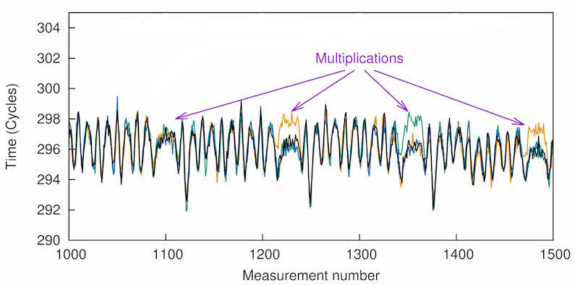
Figure 2: Multiplication takes a different execution time than other operations.
One of the most compelling such attacks on a virtualized platform was published by Thomas Ristenpart in 2009 [2]. In this attack on Amazon clouds, the adversary manages to place his VM on the same physical machine as the target VM. He then exploits the cache to extract business-sensitive information like Web site visitor statistics. More recently, Spectre and Meltdown [3] attacks have unveiled new vulnerabilities in modern processors, exploiting also their cache architecture to retrieve information from computing platforms.
Different attack techniques have been proposed to exploit cache levels of the processor, such as Prime+Probe [2], Flush+Reload [4], Flush+Flush [5], Evict+Time [6], or Flush+Abort [7]. To profile cache accesses of a victim VM or process through a shared cache, the most common attack technique is Prime+Probe (Figure 3). The attacker needs to monitor the cache activities of the victim during the execution of operations such as encryption. Although side-channel attack techniques are different, all attacks are performed in three main steps for the attacker: (1) fill one or several cache lines accessed by the victim; (2) wait for a predefined time period while the cache is used by the victim; and (3) refill cache lines with the same data used to profile the cache activities of the victim. The attacker may play with cache memory lines to refine profiling. Based on obtained activity traces, the attacker may retrieve sensitive information of the victim.
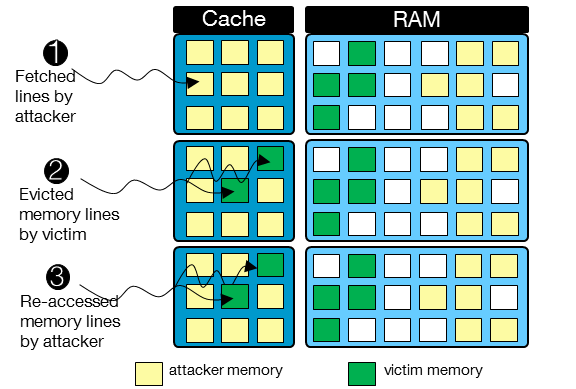
Figure 3: Different steps of a side-channel attack.
Research has demonstrated the security impact of these attacks on new cloud infrastructures. While side-channel attacks are not easy to perform because of their fine-granularity, the risk is not negligible due to improvements in attack techniques. Mitigating such attacks has thus received growing attention.
Solutions
Mitigation techniques may be divided according to the applicable infrastructure layer: application, OS/hypervisor, and hardware [1]. Application-level approaches propose new programming methods for secure implementation of cryptographic algorithms such as obscuring cache access patterns. OS/hypervisor-level approaches propose mechanisms like cache cleansing (erasing cache state) to enforce isolation between virtualized instances. Hardware-level approaches such as cache partitioning provide strong isolation, e.g., by modifying cache architecture and integrating new hardware technologies.
While all previous approaches impose performance overheads, the optimal countermeasure should still provide robust security, be scalable, and applicable to legacy infrastructures with little modifications. OS/hypervisor mitigation might be the best choice, in the infrastructure or in virtualized instances.
 As cloud provider, Orange made security a key focus of its cloud research. The goal of our research activities is to identify root causes impacting isolation between virtualized instances in novel cloud infrastructures [1] and causing new emerging classes of threats, such as distributed side-channel attacks [8]. It is also to propose new solutions to detect and to react to those attacks in current and forthcoming computing platforms, for instance combining machine learning approaches with a new hardware technology provided by Intel [9].
As cloud provider, Orange made security a key focus of its cloud research. The goal of our research activities is to identify root causes impacting isolation between virtualized instances in novel cloud infrastructures [1] and causing new emerging classes of threats, such as distributed side-channel attacks [8]. It is also to propose new solutions to detect and to react to those attacks in current and forthcoming computing platforms, for instance combining machine learning approaches with a new hardware technology provided by Intel [9].
More info:
[1] Mohammad-Mahdi BAZM, Marc LACOSTE, Mario SÜDHOLT, Jean-Marc MENAUD. Side Channels in the Cloud: Isolation Challenges, Attacks, and Countermeasures. 2017.
[2] Thomas RISTENPART, et al. Hey, you, get off of my cloud: exploring information leakage in third-party compute clouds. In : Proceedings of the 16th ACM Conference on Computer and Communications Security. ACM, 2009.
[3] Paul Kocher, et al. (2018). Spectre attacks: Exploiting speculative execution. arXiv preprint arXiv:1801.01203.
[4] Y. Yarom and K. Falkner, “Flush+Reload: A High Resolution, Low Noise, L3 Cache Side-Channel Attack,” in 23rd USENIX Security Symposium, pp. 719–732, 2014.
[5] D. Gruss, C. Maurice, K. Wagner, and S. Mangard, “Flush+ Flush: A Fast and Stealthy Cache Attack,” arXiv preprint 1511.04594, 2015.
[6] R. Spreitzer and T. Plos, “Cache-access pattern attack on disaligned aes t-tables,” in International Workshop on Constructive Side-Channel Analysis and Secure Design, pp. 200–214, Springer, 2013.
[7] Disselkoen, Craig, et al. “Prime+ abort: A timer-free high-precision l3 cache attack using intel TSX.” 26th USENIX Security Symposium (USENIX Security 17),Vancouver, BC, 2017.
[8] Mohammad-Mahdi BAZM, Marc LACOSTE, Mario SÜDHOLT, Jean-Marc MENAUD. “ Side-channels beyond the cloud edge: New isolation threats and solutions,” In : 1st. IEEE Cyber Security in Networking Conference (CSNet), 2017.
[9] Mohammad-Mahdi BAZM, Thibaut SAUTEREAU, Marc LACOSTE, Mario SÜDHOLT, Jean-Marc MENAUD. “Cache-Based Side-Channel Attacks Detection through Intel Cache Monitoring Technology and Hardware Performance Counters,” In : Third IEEE International Conference on Fog and Mobile Edge Computing (FMEC), 2018 .






