The Security of Connected Objects
Computer security is a recurring topic which is the focus of many expert articles [1] and features regularly in the news. However, even today, this essential feature is subject to minimal requirements and insufficient monitoring. This is particularly true for many types of household equipment, such as cameras, vacuum cleaners or even connected pet food dispensers [2]. However, security is improving as regulations are being put in place and proposals for new security monitoring systems throughout the life of the object are being put forward.
Let’s monitor connected devices throughout their life cycle!
Connected Objects Are Now Everywhere and Must Be Secured
The CREDOC survey reveals the increase in connected household objects. Today, one person in every three owns a connected object, 84% of French people own a smartphone, and there are, on average, eight connected devices per household. A connected device is exposed to risks, hence the importance of digital security. Although it is difficult to ascertain how many individuals fall victim to attacks, more than 50% of French companies were impacted by a cyber attack in 2021 [3] and this was predominantly through employees. Although major suppliers have been taking security into consideration, risks are being created from limited maintenance (three years for a phone) or the lack of an inspection before a sale, which can lead to equipment being misused or personal data being leaked.
Security Legislation Being Put in Place
In Europe, the Cyber Resilience Act will impose a minimum level of consideration for security on any item for sale. This will include appointing a contact person in the event of a problem, enforcing a mandatory update system, verifying that there are no critical vulnerabilities at the time of sale, and ensuring that the item has five years of maintenance. Although it might not be expected to be become law until 2024, the Act marks a major step forward in the field of connected objects. Moreover, at French and global level, AFNOR is working on an ISO standard for an IoT security rating system that will allow users to identify any objects at risk. For websites, a Cyber Score will be rolled out for the main platforms across France in 2023, to indicate privacy and security risk levels.
Current System Limitations
The security of an object is mainly implemented during its design, as part of an approach called Security by Design. This security is essential and is being enforced by the new regulations. However, this security remains rather limited once the object is released, as any updates rely on the manufacturer’s goodwill and the maintenance guarantee. Nowadays, certain devices such as TVs are kept for over seven years on average [4] and, in an attempt to become more frugal, people prefer to keep their equipment for longer — a trend that is not always rewarding for manufacturers with a preference for selling new devices. This shows how these scores are not yet sufficient when it comes to security. Vulnerabilities are exposed on a daily basis, leading to new risks that can shift from the digital world to the real world. One such example would be a burglar using a thermostat or TV to monitor whether a house is occupied, before breaking in.
New Tools to Improve Security Monitoring
Orange is playing a role in implementing these scores and, as part of its research projects, is also working on a visualization tool to continuously monitor the security risks of all household equipment, whether it be a connected plug, a cell phone or a computer. This tool provides guidance to help users keep their equipment secure. For example, it could help them to install an update, uninstall an application, cut off remote access to certain equipment or even isolate it. This tool would be included with Livebox in order to carry out monitoring locally and would be activated by those wishing to control their devices. It would always remain under the user’s control to prevent the necessary functionalities from being lost. As well as carrying out monitoring, this tool provides a continuously updated score for each device, which makes it easy to view risks.
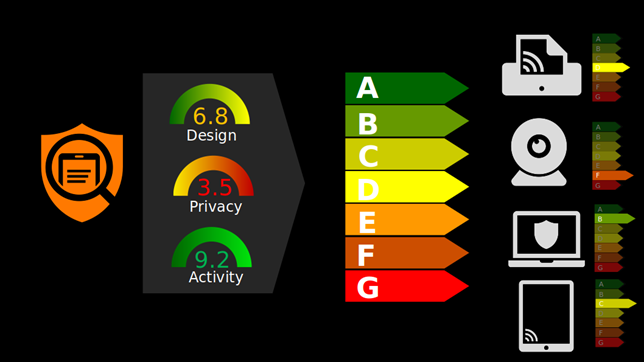
A Score That Checks Every Aspect of Security
Developed during the research project, this continuous score has three underlying components. The first is called “Design” and focuses on the risks related to the design of an object with software faults, the verification of the system maintenance and the removal of unwanted applications. The second component, “Privacy”, checks that the object does not distribute personal information over the network and whether the information communicated externally is sent via GDPR-compliant servers and with a protocol guaranteeing that data is not intercepted. The third and final component, “Activity”, is linked to any equipment being accessed externally. It checks that a server is not compromised and that the protocols used are not obsolete. These three components are then combined into a single score that is continuously updated. Like the Nutri-Score, the weighting between the different components depends on the type of equipment and the type of risk for the user, whether this is measured by the data processed or its use. This score applies to all connected equipment, from phones to cameras.
A System That Respects Confidentiality
With the security of objects being constantly monitored comes many questions about privacy. If the tool that monitors the security of objects is itself at risk for the processed data, this would not improve the user’s security. This monitoring system is therefore local and as close as possible to users and objects. Not only does this improve the relevance of the results, it also guarantees that privacy is respected by processing the data in such a way that it does not need to be distributed externally. As a trusted provider, Orange’s mission is to enable everyone to access digital tools securely. As a carrier and a home access point, Orange can provide security for household equipment.
Sharing Audit Results
With the users’ consent, this equipment monitoring system could also anonymously report their objects’ score to a data repository. If available on purchase support platforms or on a dedicated space, this evolving and constantly updated Cyber Score could help inform users purchasing objects. It could also allow manufacturers to become increasingly aware of security issues.











